Ransomware scum are using an SMB exploit leaked by the Shadow Brokers last month to fuel a massive ransomware outbreak that exploded online today, making victims all over the world in huge numbers.
The ransomware's name is WCry, but is also referenced online under various names, such as WannaCry, WanaCrypt0r, WannaCrypt, or Wana Decrypt0r. As everybody keeps calling it "Wana Decrypt0r," this is the name we'll use in this article, but all are the same thing, which is version 2.0 of the lowly and unimpressive WCry ransomware that first appeared in March.
Activity from this ransomware family was almost inexistent prior to today's sudden explosion when the number of victims skyrocketed in a few hours.
Wana Decrypt0r uses NSA's ETERNALBLUE exploit
What was clear about this ransomware was that Wana Decrypt0r was extremely virulent. The one who unraveled the mystery was French security researcher Kafeine, who was the first to spot that Wana Decrypt0r triggered security alerts for ETERNALBLUE, an alleged NSA exploit leaked online last month by a nefarious group known as The Shadow Brokers.
ETERNALBLUE works by exploiting a vulnerability in the SMBv1 protocol to get a foothold on vulnerable machines connected online. Microsoft patched the flaw in MS17-010, released in March, but that doesn't mean all Windows PC owners have applied the security update.
Unpatched Windows machines exposed online today risk being exploited with ETERNALBLUE, and then infected with Wana Decrypt0r.
UPDATE: After this article's publication CERT Spain and other security experts confirmed seeing the Wana Decrypt0r actors also dropping the NSA's DOUBLEPULSAR malware on infected systems as well. This is a Windows kernel Ring-0 exploit — also developed by the NSA and leaked by the Shadow Brokers — that was used by an unknown actor in late April to infect over 36,000 computers worldwide. DOUBLEPULSAR is what's called a "malware loader," used to download and install other malware.
Over 57,000 Wana Decrypt0r infections detected
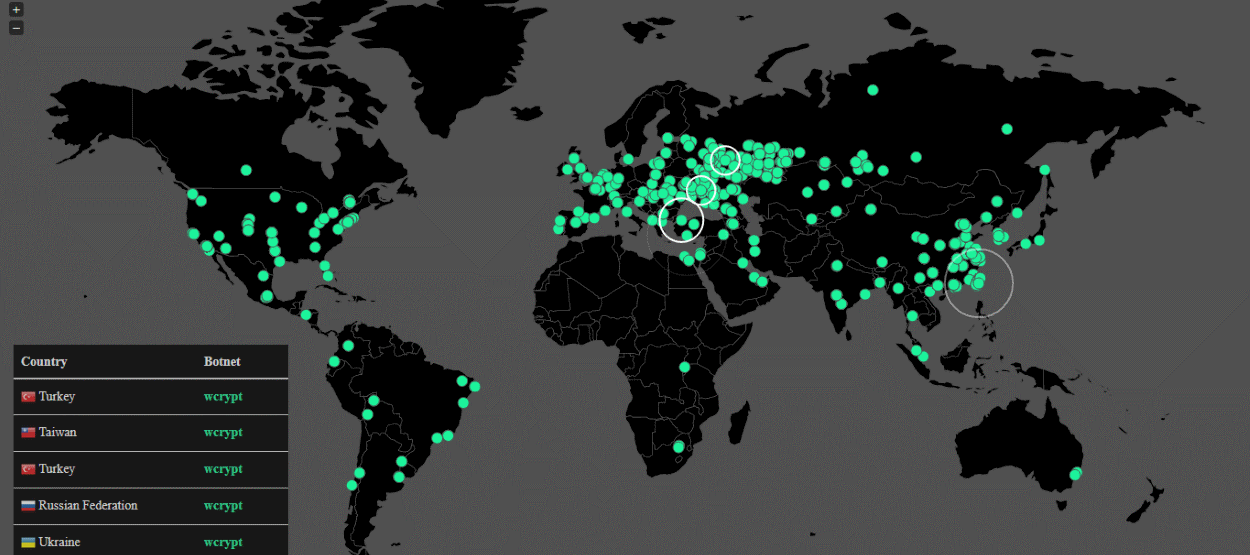
CERT Spain and security researcher MalwareTech have confirmed Kafeine's original findings. The latter even created a live map showing new Wana Decrypt0r victims infected in real time.
Whoever is behind this ransomware has invested heavy resources into Wana Decrypt0r's operations. In the few hours this ransomware has been active, it has made many high-profile victims all over the world. According to Avast security researcher Jakub Kroustek, Wana Decrypt0r made over 57,000 victims in just a few hours.
Some of the first victims were Spanish companies, such as Telefonica — a telco provider, Gas Natural — a natural gas provider, and Iberdrola — an electric utility provider.
Later in the day, the wave of Wana Decrypt0r infections spread to the UK, where it hit a large number of hospitals and clinics. UK's the National Health Service issued an alert on the attacks earlier today.
Shocking that our @NHS is under attack and being held to ransom. #nhscyberattack pic.twitter.com/1bcrqD9vEz
— Myles Longfield (@myleslongfield) May 12, 2017
A ransomware spreading in the lab at the university pic.twitter.com/8dROVXXkQv
— PlayNierAutomata (@dodicin) May 12, 2017
Just got to Frankfurt and took a picture of this... #Sbahn, you got a #Ransomware! pic.twitter.com/w0DODySL0p
— Marco Aguilar (@Avas_Marco) May 12, 2017
Other victims also include the Russian Interior Minister, Portugal Telecom, and a large number of universities in China.
In the meantime, Bleeping Computer has learned from an inside source that Telenor Hungary — a local telecommunications provider — also suffered a similar incident. Just like Telefonica, had issued an SMS alert warning customers to shut down PCs or disconnect them from internal VPN networks. Another source also told Bleeping Computer that FedEx's Memphis office is currently telling employees to shut down their PCs in a somewhat similar incident.
By the end of the day, Kaspersky Lab reported that 3 out of 4 Wana Decrypt0r infections were occuring in Russia, by far the most targeted country.
Astime goes by, we expect the number of Wana Decrypt0r victims to rise over the course of the next few days. Whatever happens, the operators of this ransomware have made a name for themselves and carved a place for their malware in infosec lore.
Last month, the developer of the AES-NI ransomware claimed his ransomware also used the ETERNALBLUE exploit. Infections with AES-NI spiked over a weekend, but died down after and was never heard from again.
For those affected, you can discuss this ransomware and receive support in the dedicated WanaCrypt0r & Wana Decrypt0r Help & Support Topic. Bleeping Computer also published a technical analysis of the Wana Decrypt0r ransomware.
UPDATE [May 12, 2017, 08:05 PM ET]: The spread of the Wana Decrypt0r ransomware has been temporarily stopped after security researcher MalwareTech has registered a hardcoded domain included in the ransomware's source code. Wana Decrypt0r connected to this domain (iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com) before it started its execution. The check was strange. The ransomware checked if the domain was unregistered, and if it was, it would execute. If it wasn't, it would stop spreading, acting like a kill switch. With MalwareTech registering the domain, the ransomware now does not start anymore. Cisco Talos has confirmed the information.
UPDATE [May 12, 2017, 08:58 PM ET]: While the spread of the worm has been temporarily stopped by MalwareTech's registration of one of the hardcoded C2s, this is just a temporary measure. It would be trivial to modify the ransomware to use different domains and the process starts again. As BleepingComputer and MalwareTech state, the only solution is to make sure you have all your Windows security updates installed!
UPDATE [May 13, 2017, 09:15 AM ET]: The Wana Decrypt0r attacks have been so vicious, that it convinced Microsoft to issue updates for operating systems it stopped supporting years before, such as Windows XP, Windows Server 2003, and Windows 8.
Image credit: MalwareTech


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now